The NIS 2 Directive: what does it mean for my organization?
NIS2 Directive (Background information)
Since 16 January 2023, what is termed the NIS 2 Directive has been in effect.
(Directive (EU) 2022/2555 of the European Parliament and of the Council of 14 December 2022 on measures to ensure a high common level of cybersecurity in the Union (amending Regulation (EU) No 910/2014 and Directive (EU) 2018/1972 and repealing Directive (EU) 2016/1148)
1. Background
2. Does NIS 2 apply to my organization?
2.1 New sectors
2.2 New concepts
2.3 Jurisdiction and territoriality
3. Strengthening cybersecurity risk management measures
4. Reporting and incident reporting obligations
5. Sanctions
6. Way forward
Based on the new Directive, Belgium will have to adopt new provisions to replace the existing NIS Act by 17 October 2024. Work to prepare for the transposition will take place in the coming months.
1. Background
This NIS 2 Directive is the successor to the 2016 NIS 1 Directive (transposed in Belgium mainly in the NIS 1 Act of 7 April 2019). It was proposed by the European Commission in December 2020. After the negotiation process, it was officially approved by the Council and the European Parliament on 14 December 2022, and officially published on 27 December 2022. Each EU Member State now has until 17 October 2024 to transpose the NIS 2 Directive into its national legislation.
In a blog post last year, we explained why the NIS 1 Directive needed an update and what some of the key discussion points were.
In essence, the NIS 2 Directive aims to achieve the same three goals as its predecessor:
- Require national governments to pay due attention to cybersecurity;
- Strengthen European cooperation among cybersecurity authorities;
- Require the main operators in key industries of our society to take security measures and report incidents.
Given the increased cyber threat and our society's greater reliance on network and information systems since 2016, the NIS 2 Directive is broader than the NIS 1 Directive in many ways. This is what European Commissioners already expressed hope for in December 2020, when they launched the initiative as the cornerstone of the European Cybersecurity Strategy: "NIS 2 is NIS 1 on steroids".
National governments (including the national CSIRT) are required to have more clout and must cooperate more; national cybersecurity strategies must include more elements (including the concept, important for Belgium, of Active Cyber Protection, and a specific policy for SMEs); and each Member State must set up a coordinated vulnerability disclosure framework, and have cybersecurity crisis management frameworks and authorities (see Articles 7-13 of NIS 2 in this respect).
European cooperation is also being expanded, at the policy level (through the NIS Cooperation Group), at the technical level (in the EU CSIRTs network), and at the crisis management level (through the creation of the Cyber Crisis Liaison Organisation Network, or CyCLONe). Member States will have to undergo regular Peer Reviews; the European agency ENISA will publish a Cybersecurity State of the Union every two years; and there will be a European vulnerability database (see about all this in Art. 12 + 14-19).
The biggest innovation is for the third objective: a huge expansion of the number of entities and sectors in scope; more specifications of measures; more extensive rules around incident reporting; higher and more specific sanction rules; and assigning responsibility to the senior management of each entity so that cybersecurity can become a real boardroom issue.
2. Does NIS 2 apply to my organization?
The scope of the NIS 2 Directive has been greatly expanded from that of the NIS 1 Directive and is no longer necessarily linked to prior identification by the competent national authorities of the entities concerned.
Essentially, an entity is covered by the scope if it:
- operates in one of the (sub)sectors and types of services listed in the annexes of the Directive,
and - is of a certain size.
For all the details, exceptions and nuances, see the "new concepts" section below and Articles 2 & 3 and Annexes I & II of the Directive.
2.1 New sectors
The NIS2 Directive adds new sectors, but it also adds types of entities within existing sectors. The sectors are divided into two groups.
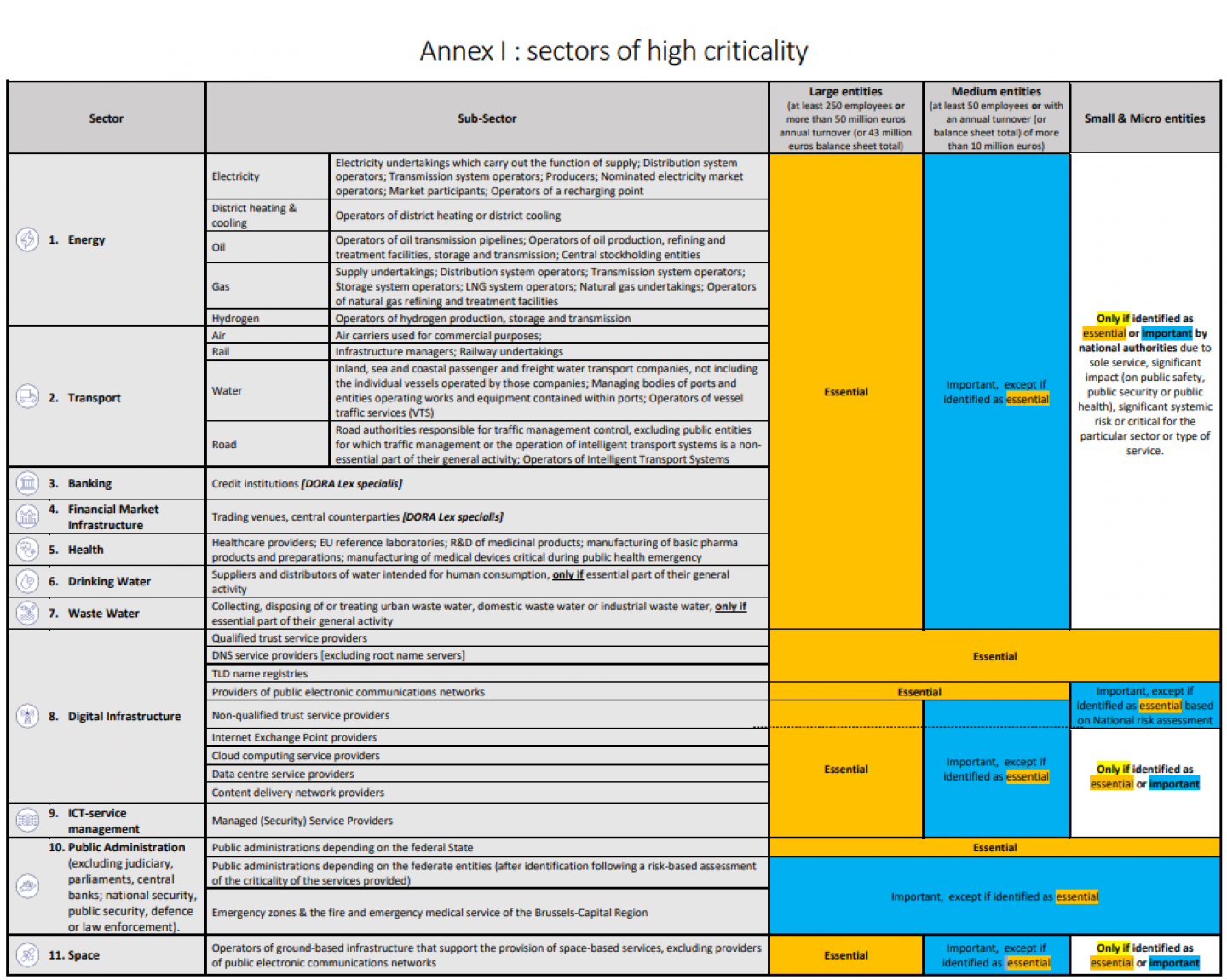
The sectors of high criticality (see Annex I of the Directive) are:
- Energy (electricity, district heating and cooling, petroleum, natural gas, hydrogen)
- Transport (air, rail, water, road)
- Banking
- Financial market infrastructure
- Health (which no longer only includes hospitals but now also includes reference laboratories, medical device or pharmaceutical preparation manufacturers and others)
- Drinking water
- Waste water
- Digital infrastructure
- ICT service management
- Public administration (central and regional)
- Space
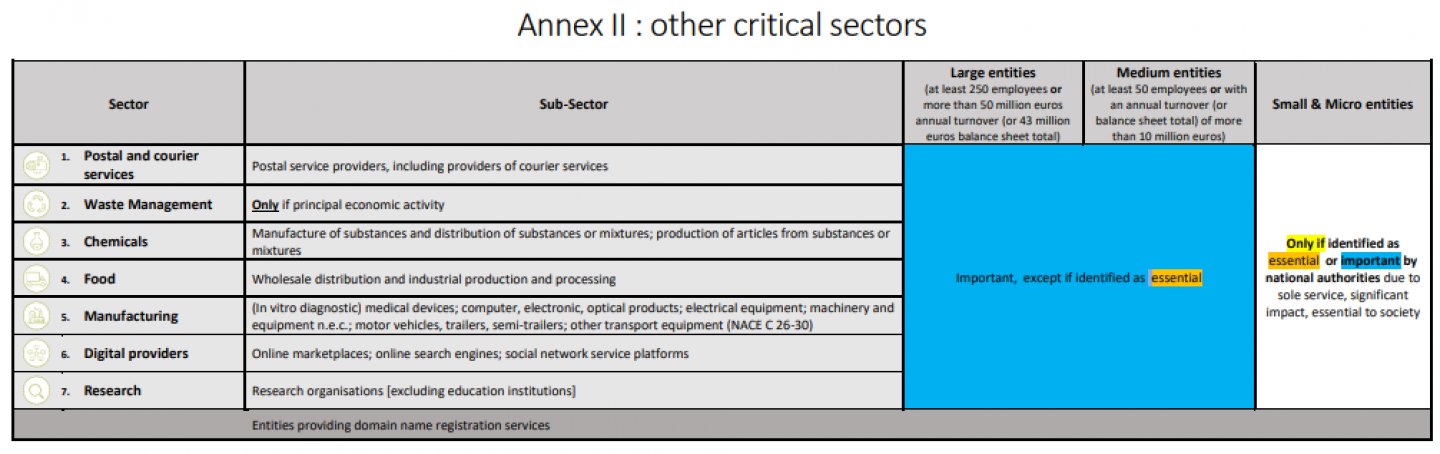
Other critical sectors (see Annex II of the Directive) are:
- Postal and courier services
- Waste management
- Manufacture, production and distribution of chemicals
- Production, processing and distribution of food
- Manufacturing (of medical devices and in vitro diagnostic medical devices; computer, electronic and optical products; electrical equipment; machinery and equipment n.e.c., motor vehicles, trailers and semi-trailers; other transport equipment)
- Digital providers
- Research
2.2 New concepts
Barring exceptions, there is no longer active identification in NIS 2. An entity operating in the sectors listed above is in scope if it is a large or medium-sized enterprise. That is, it has more than 50 employees or an annual turnover of over €10 million (see Commission Recommendation of 6 May, 2003 No. 2003/361 concerning the definition of micro, small and medium-sized enterprises - [link] http://data.europa.eu/eli/reco/2003/361/oj).
With specific exceptions, small and micro enterprises (with fewer than 50 employees and an annual turnover (or annual balance sheet total) of less than €10 million – cumulative conditions) are excluded from the scope of the Directive.
The former distinction between "operators of essential services" (OES) and "digital service providers" (DSP) disappears and is replaced by a distinction between "essential" and "important" entities. This distinction is made automatically based on the size of the entity and the type of entity involved.
The difference between essential and important entities is mainly in the stringency of supervision and sanctions. Essential entities will be more tightly controlled and sanctioned than important entities (see below).
Essential entities are large companies* that are part of the sectors of high criticality listed in Annex I of the Directive. A large entity is defined as a company with at least 250 employees OR with an annual turnover of at least 50 million euros or an annual balance sheet total of at least 43 million euros.
Important entities are medium-sized enterprises* operating in the sectors of high criticality of Annex I of the Directive, OR large* or medium-sized* enterprises in the sectors of Annex II of the Directive that do not fall into the essential entity category (due to their size or the type of entity involved). A medium-sized enterprise is defined as one with at least 50 employees OR with an annual turnover (or balance sheet total) of at least 10 million euros, but with fewer than 250 employees AND no more than 50 million euros annual turnover or 43 million euros balance sheet total.
However, there are some exceptions. In some sectors, entities, regardless of size, are designated as "essential", for example, providers of public electronic communications networks, entities designated as critical at the national level under the Block Exemption Regulation, government services (at the central level), qualified trust service providers and top-level domain name registries and DNS service providers.
Apart from these rules, national authorities may also specifically designate entities as "essential" or "important," such as when they are the sole service provider or when a disruption in service provision could have significant consequences for public safety, public security or public health.
All this together is a fairly complex system of scope. It is important to reiterate, however, that this contains only the rules of European minimum harmonization. In the Belgian transposing legislation, further or stricter specifications can be introduced.
For full details on all these points, see specifically Articles 2, 3 and 4 of the Directive.
2.3 Jurisdiction and territoriality
In principle, the Belgian legislation transposing the NIS 2 Directive will apply to entities based in Belgium. The recitals of the Directive state that an establishment "implies the effective exercise of activity through stable arrangements. The legal form of such arrangements, whether through a branch or a subsidiary with a legal personality, is not the determining factor in that respect. Whether that criterion is fulfilled should not depend on whether the network and information systems are physically located in a given place.” (Recital 114).
However, there are exceptions to this rule of territorial jurisdiction:
- Providers of public electronic communications networks or providers of public electronic communications services are subject to the jurisdiction of the Member State in which they offer their services;
- DNS providers, registries of top-level domain names, entities offering domain name registration services, cloud computing service providers, data centre service providers, content delivery network providers, managed service providers, managed security service providers, as well as providers of online marketplaces, online search engines or social networking service platforms are subject to the jurisdiction of the Member State in which they have their principal place of business in the EU. (See Article 26(2) of the Directive to know how the main establishment is determined).
- Public administration entities are under the jurisdiction of the Member State that created them;
For entities subject to the main establishment rule, ENISA will maintain a central registry to ensure effective oversight of all entities operating in the EU. Finally, since the largest group of entities are no longer actively identified, they will have to register so that each Member State has a complete list of all NIS 2 entities under their jurisdiction.
For full details on all these points, see specifically Articles 26-27 of the Directive.
3. Strengthening cybersecurity risk management measures
Essential and important entities covered by the scope must take appropriate and proportionate measures to manage the risks to the security of their network and information systems, and to prevent incidents or mitigate the effects of incidents on the recipients of their services and on other services (see especially Art. 20-25).
These measures are based on an all-hazards approach that aims to protect network and information systems and the physical environment of those systems from incidents.
At a minimum, these measures include:
- Risk analysis and information systems security policies;
- Incident handling;
- Business continuity, such as backup management and disaster recovery, and crisis management;
- Supply chain security, including security-related aspects concerning the relationships between each entity and its direct suppliers' or service providers' security in network and information systems acquisition, development and maintenance, including vulnerability handling and disclosure;
- Policies and procedures to assess the effectiveness of cybersecurity risk-management measures;
- Basic cyber hygiene practices and cybersecurity training;
- Policies and procedures regarding the use of cryptography and, where appropriate, encryption;
- Human resources security, access control policies and asset management;
- The use of multi-factor authentication or continuous authentication solutions, secured voice, video and text communications and secured emergency communication systems within the entity, where appropriate.
The governing bodies or executives of essential and important entities must approve cybersecurity risk management measures, and oversee their implementation, and may be held liable for any breaches.
To ensure that they understand what measures they are adopting, members of the governing bodies of essential and important entities should undergo cybersecurity training and provide similar training to their employees on a regular basis. Managers must acquire sufficient knowledge and skills to identify risks to their organization and to assess cybersecurity measures and their impact on their organization.
The European NIS Cooperation Group will soon update its guidelines on security measures to clarify the practical scope of the different security objectives in the Directive (see previous reference document "Reference document on security measures for Operators of Essential Services" [link]
At the national level, competent authorities will be able to describe more precisely and practically how these security requirements are to be met.
In addition, the European Commission will adopt an implementing act setting out the technical and methodological requirements for cybersecurity risk management measures for all entities covered by the main establishment scheme (see above).
If necessary, the European Commission may also adopt an implementing act containing technical and methodological rules, as well as sector-specific rules, for other important and crucial entities.
The EU can also subsequently impose more specific requirements, for example through mandatory certification. Furthermore, the EU may conduct coordinated risk assessments, especially for critical supply services or products, which may lead to more action. Thus, companies are not just at the mercy of contractual dependence on key suppliers.
For full details on all these points, see specifically Articles 20-25 of the Directive.
4. Reporting and incident reporting obligations
Essential and important entities must report any significant incident without delay to the competent national authorities (including the national CSIRT – in Belgium, the CCB).
Essential and important entities must immediately notify the competent national authorities (including the national CSIRT – in Belgium, the CCB) of any incident that seriously affects services in the sectors or sub-sectors listed in Annexes I and II of the Directive.
A significant incident is one that:
1° has caused or is capable of causing serious operational disruption to services in the sectors or subsectors listed in Annexes I and II of the Directive or financial losses to the entity concerned; or
2° has affected or is capable of affecting other natural or legal persons by causing considerable material or non-material damage.
This notification should consist of several steps:
- Early warning (no later than 24 hours of learning of the incident), with minimal info, including whether the incident may spread to other sectors or abroad, and whether malicious intent is suspected;
- A complete incident report (no later than 72 hours of learning of the incident)
- Possibly an interim or progress report (at the request of the national CSIRT).
- A final report (one month after submission of the incident report). If the incident is not yet over after 1 month, an interim report is expected after 1 month, and a final report once the incident is over.
Where applicable, an entity must also promptly notify their customers of significant incidents that could harm their services.
In addition to the reporting requirement, reports may be submitted on a voluntary basis by:
- Essential and important entities, reporting on (non-significant) incidents, cyber threats and prevented incidents;
- Entities other than essential and important entities, whether or not they fall within the scope of the Directive.
For more details on reporting requirements, see Articles 23 and 30 of the Directive, among others.
5. Sanctions
Member States must efficiently ensure that entities in the scope of NIS 2 take the necessary measures and report incidents. To do this, they may, for example, conduct regular external audits or inspections, or request certain documentation.
Competent national authorities should also have the power to take action to encourage entities to take appropriate measures. This can range from issuing warnings or binding instructions to correct deficiencies, and informing their customers. In addition to these administrative measures, effective, proportionate and dissuasive administrative fines may also be imposed.
Violations of risk management measures or incident reports can be penalized:
- For essential entities: with administrative fines of up to €10,000,000 or at least 2% of the total annual worldwide turnover in the previous fiscal year of the company to which the essential entity belongs, whichever amount is higher.
- For important entities: administrative fines of up to €7,000,000 or at least 1.4% of the total annual worldwide turnover in the previous fiscal year of the company to which the important entity belongs, whichever amount is higher.
For the public sector, the transposing legislation may provide that the administrative fines do not apply to public administration entities. However, the other administrative sanctions will apply.
Member States may also provide for the power to impose periodic penalty payments to compel an essential or important entity to cease an infringement of the Directive in accordance with a prior decision of the competent authority.
To motivate compliance with the obligations in this Directive from senior management, natural persons representing essential entities may be held liable for failure to comply.
For full details on sanctions, see Articles 31-37 of the Directive.
6. Way forward
Based on the new Directive, Belgium will have to adopt new provisions to replace the existing NIS Act by 17 October 2024. Work to prepare for the transposition will take place in the coming months.
In any case, the new obligations for relevant entities should not come into effect until the end of the transposition period (October 2024). However, it is useful for companies to prepare now for the general obligations arising from the Directive, without waiting for the transposing legislation, taking into account the increasing threats and risks. Therefore, we can only advise entities that will clearly be subject to these new obligations to begin raising (or continuing to raise) their level of cybersecurity from now.
The CCB has published a Cyberfundamentals framework with specific audit objectives. This tool can help and advise companies to raise their security to an appropriate level right away.