13 million clicks to suspicious websites prevented in 2022
In 2022, collaboration with the public prevented no less than 13 million clicks to suspicious websites, or about 25 warnings to Internet users per minute.
The Belgium Anti-Phishing Shield (BAPS) is a system designed by the Centre for Cybersecurity Belgium (CCB) to warn Internet users surfing to dangerous websites.
For many years now, the CCB has been able to rely on the cooperation of the public through the notification of suspicious messages. Every day we receive thousands of suspicious e-mails. In 2021, 4,500,000 messages were forwarded to suspicious@safeonweb.be. In 2022, this figure rose further to 6 million messages, resulting in the detection of more than 1.5 million suspicious URLs, an average of 15,000 messages analysed per day.
Suspicious URLs in these emails are passed on to Google SafeBrowsing and Microsoft SmartScreen. The browsers then use this information to warn people about malicious websites. Since we have no control over the speed at which Google and Microsoft block these links, the CCB and the Internet service providers Belnet, Proximus, Telenet and Orange have managed to develop their own system and a procedure to warn Internet users in real time: the Belgium Anti-Phishing Shield (BAPS).
The Belgian Cybersecurity Centre asks the public to continue to forward suspicious messages to suspicious@safeonweb.be. The speed with which messages are sent helps to minimise the number of victims. A less attentive person who might be tempted to click on a link will end up on a warning page. BAPS cannot be effective without the public sending suspicious messages.
It is also possible to send a screenshot of fraudulent SMS and QR code messages. Our technology is able to detect URLs in images and QR codes.
What is the Belgium Anti-Phishing Shield or BAPS?
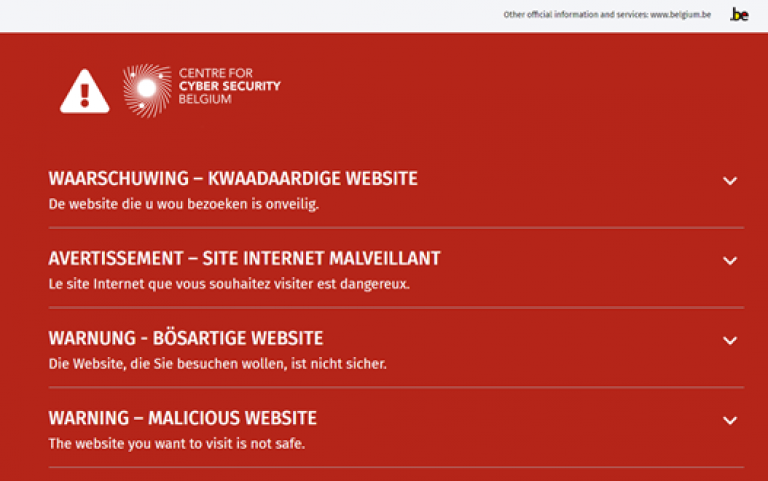
The Belgium Anti-Phishing Shield (BAPS) warns the population about malicious links sent to the CCB via suspicious@safeonweb.be. The BAPS was tested in 2021 and was gradually made available to the public.
When a user in Belgium clicks on a link, the request to view the web page is sent to their Internet Service Provider (ISP). The ISP then checks with BAPS whether the domain (website) the user wants to access is not on a list of malicious domains. If it is, the ISP server will redirect the user to a warning page.
How is this list of malicious websites built up?
The list of malicious websites is built up from the thousands of suspicious messages sent by citizens to suspicious@safeonweb.be every day. The Internet domains that appear in these messages are automatically evaluated and very quickly forwarded to the Internet service providers - the sooner, the better! A thorough evaluation prevents a legitimate website from appearing on this list by mistake, whereas BAPS is aimed exclusively at phishing. Only sites that have been designated as "dangerous" are included in the list.
How does BAPS work?
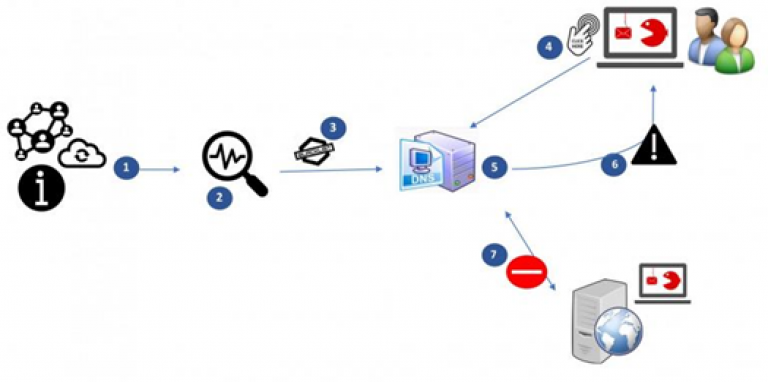
- The CCB receives information about potentially malicious websites via suspicious@safeonweb.be;
- Potentially malicious websites are analysed and listed;
- The list of malicious websites is passed on to the Internet service providers;
- The Internet user clicks on the malicious URL;
- The Internet provider checks whether the site that is the subject of the DNS request is on the list of malicious Internet sites (domains);
- If this is the case, the user is redirected to a warning page;
- The Internet user does not access the malicious website.

